While checking Detectify Lab, I came across XSS Vulnerability on MEGA.CO.NZ which was found by Frans Rosen so I though of doing some test on MEGA but I ended with none. I didn’t give up ! after a while I thought of scanning & looking into sub domain of both mega.nz and mega.co.nz and found out eye catching sub-domain.
And it was https://stats.admin.mega.nz/
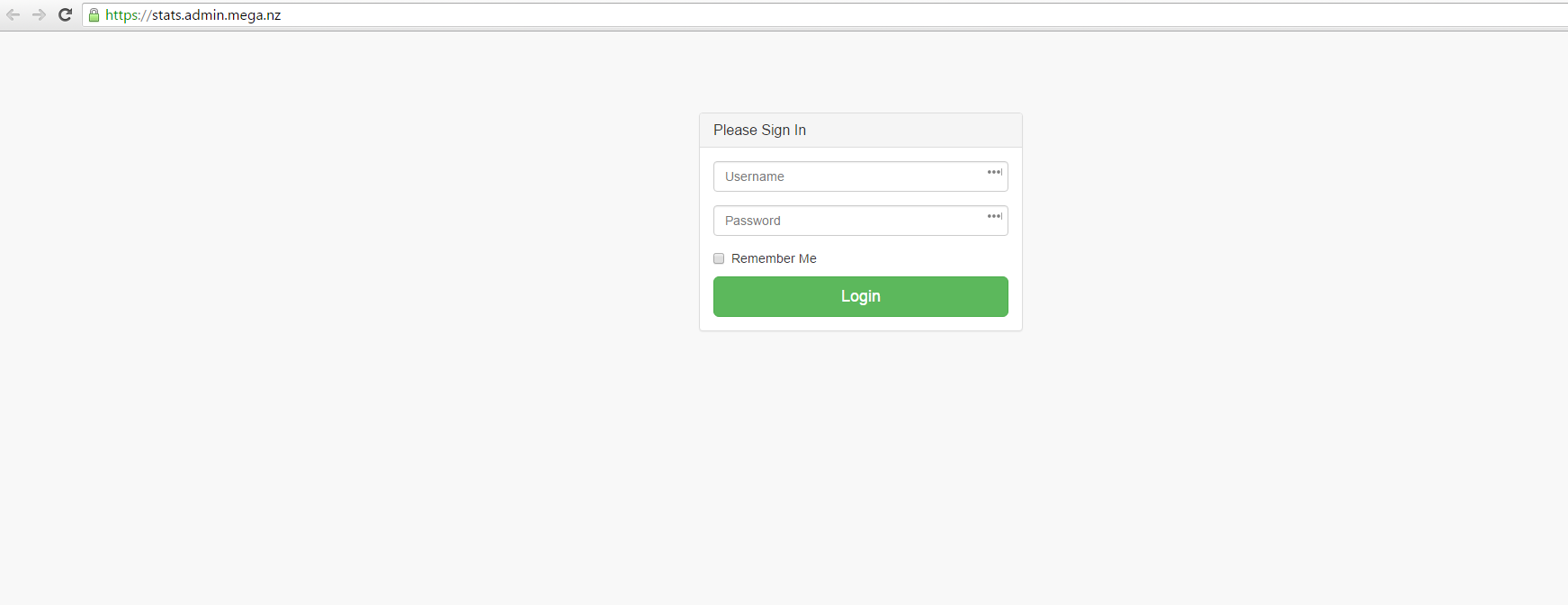
I entered the random logins credential,
POST / HTTP/1.1 Host: stats.admin.mega.nz User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:44.0) Gecko/20100101 Firefox/44.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate, br Referer: https://stats.admin.mega.nz/ Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 37 username=admin&password=admin
But no luck and then I added ( ‘ ) to the parameters and it was like :
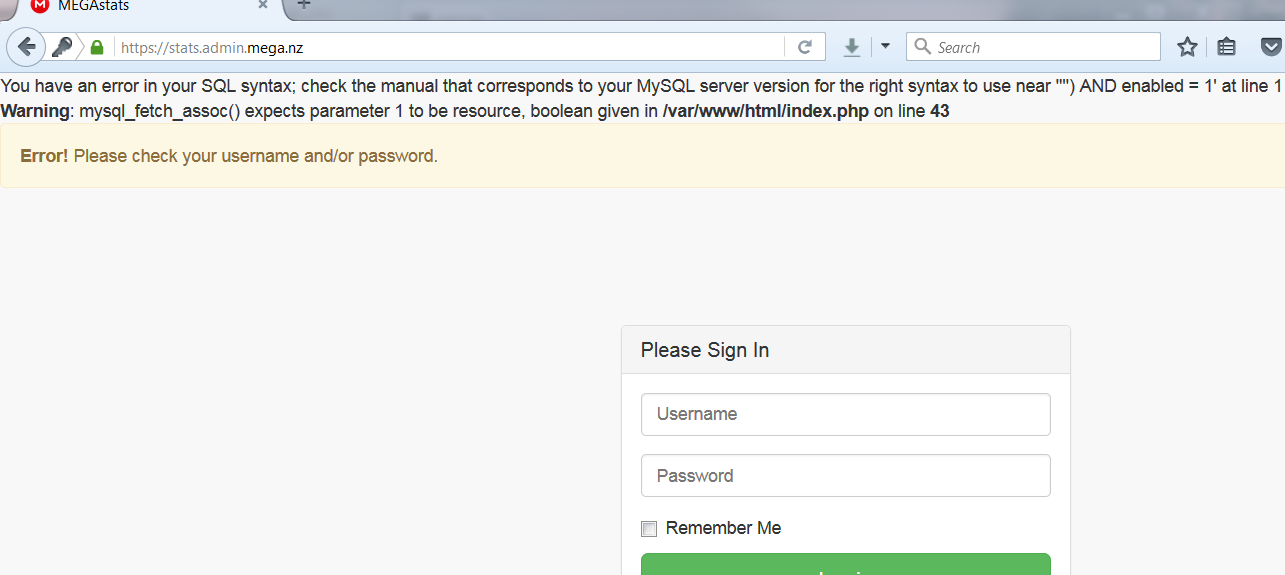
Without any delay, I reported to MEGA at [email protected]
I sent an email at 3:10 PM and after a few minutes I got a reply with :
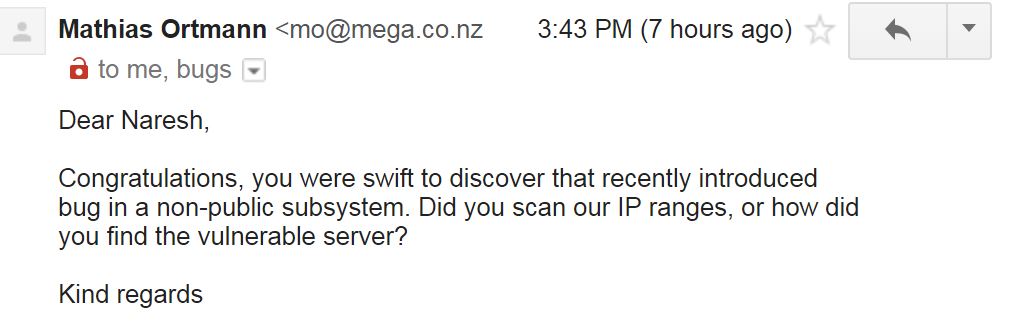
#meganz that was the quickest bug fix I have ever seen. 30 min. that was way damn awesome. (y) good job #meganz
— NȺɌɆSĦ ŁȺMǤȺĐɆ (@nlamgade) March 10, 2016
And later :
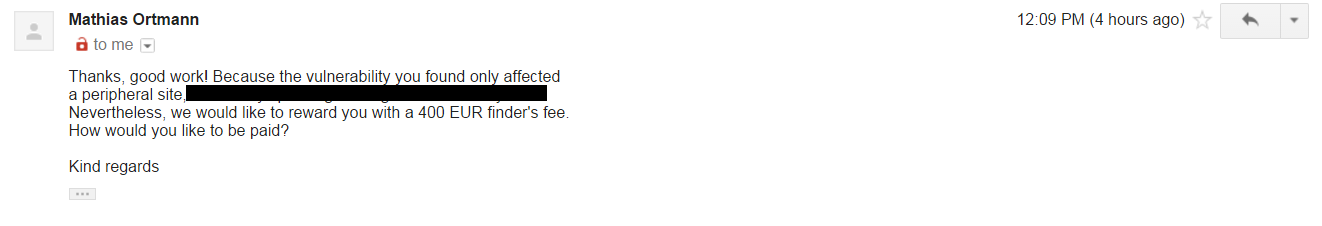
Nice, they fixed the bug within 30 minutes! and they rewarded me 400 EUR as a bounty.
That was the fastest fix I have ever encountered and I am really thankful for bounty. 🙂
Cheers for MEGA !
UPDATE : Again I checked that site for the bug after few months and still it was there and again I reported and again another bounty. :v
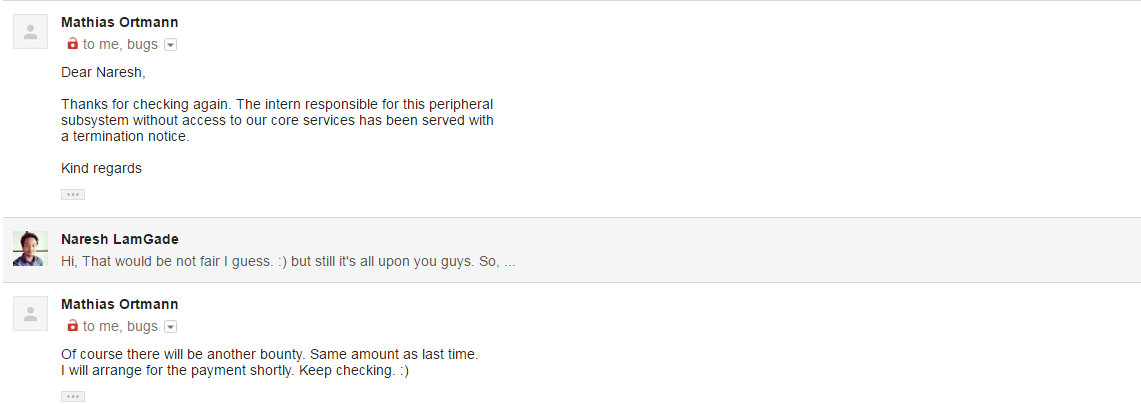
SO ANOTHER 400 euro
Tips:
- Keep on looking for old issues on time to time as there might be many changes on the codebase so bugs might come up again.
- Don’t judge target on the basis of bug submitted as there will be always bugs, you just need to find out and for that, keep on digging.
- Never give up.
 Naresh LamGade
Naresh LamGade